
Phishers, the criminals who try to trick you into giving them access to your devices, continue to hone their attacks. You do the work for them, with no complicated hacking required on their part.
Microsoft's Threat Intelligence researchers have uncovered one such clever phishing campaign that has been targeting hotel staff since December last year, just in time for peak travel season.
The scam is still going strong as we head into March, Microsoft said, and happening in our part of the world.
Booking.com is the site used as a lure, with hotel staff being sent emails about guest reviews or booking requests that arrive from legit mail services like Gmail and iCloud (but not Outlook.com? Really, Microsoft?)
What makes this attack particularly devious is how it exploits the relationship between hotels and the online booking giant. Hotel staff are used to dealing with Booking.com requests daily, making these fake emails that much more likely to slip through human defences.
The criminal group behind this, tracked by Microsoft as "Storm-1865," has been fine-tuning their approach. They've added what security researchers call a "ClickFix" technique – essentially tricking users into fixing a non-existent problem which, when people follow the steps to remedy the issue, actually installs malware.
Here's how it works:
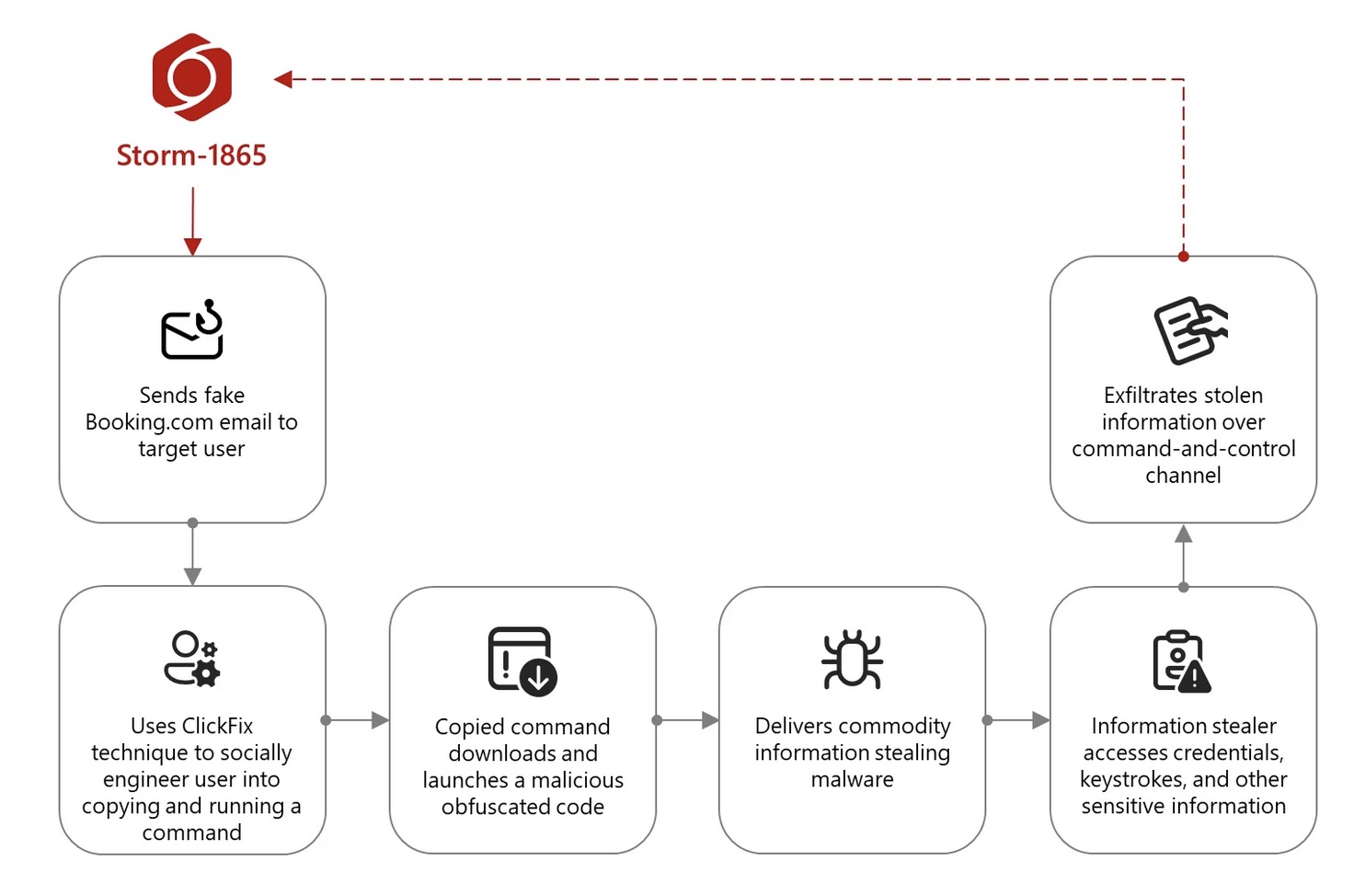
It's a fascinating bit of social engineering. The fake webpage used by the attackers displays a CAPTCHA with an error message, then instructs the user to press a Windows-Run keyboard shortcut and paste a command.
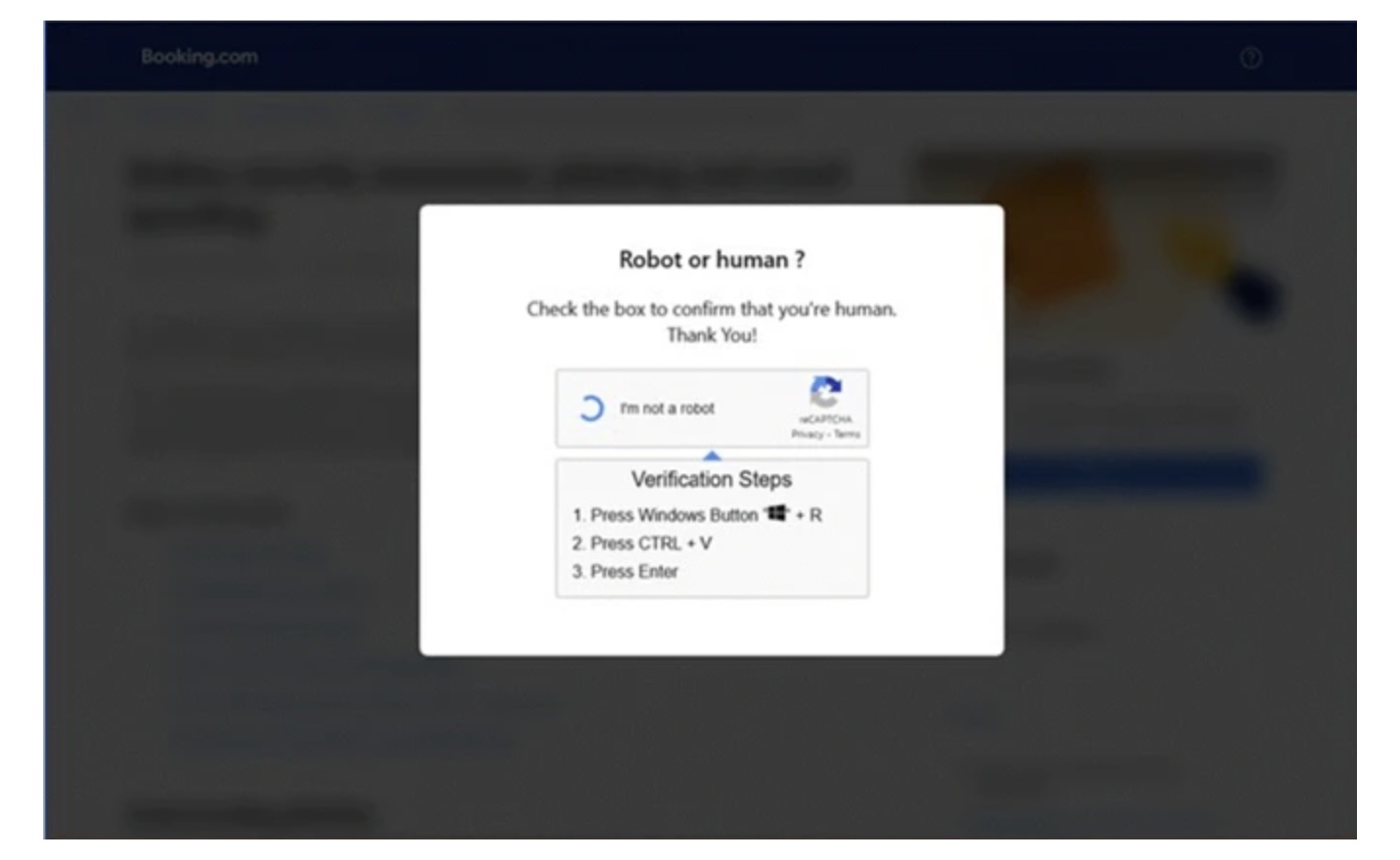
What users don't realise is that the webpage has secretly copied the malicious command to their operating system's clipboard, ready to be pasted and executed.
I've seen many phishing techniques over the years, and this one stands out for its psychological manipulation which is very devious indeed. As Microsoft says, it exploits our natural tendency to follow troubleshooting steps, especially when presented by what appears to be a legitimate website.
The malware payload isn't just a one-trick pony either. Microsoft has so far identified six different types of credential-stealing malware being deployed, with names like XWorm, Lumma stealer, and NetSupport RAT (remote access tool, which does exactly what the name implies). All these code nasties are designed to pilfer financial data and login credentials for later fraud.
For hotel operators, especially smaller establishments that might not have dedicated IT security teams, this represents quite a serious threat. Once credentials are stolen, the attackers can potentially access booking systems, payment details, and customer information.
Microsoft recommends the usual security hygiene: multi-factor authentication, careful examination of email senders, and verifying links before clicking. They've also published technical threat indicators for security teams in larger organisations to watch out for.
Storm-1865 has shown they're adaptable since first appearing on the security radar in 2023. In previous years, they targeted hotel guests directly, and now they've shifted focus to the hotels themselves. At this stage, there's no clear indication as to the attackers' identity.
As a related aside, security researchers use particular naming conventions to track threat actors. They quite often differ between security vendors with the names sometimes being taken from the group’s malware code, and they can be pretty weird. In this case, Microsoft uses the Storm prefix for developing threat groups, followed by a number.
So yes, we should stop clicking on links in emails. And no, that's not going to happen any time soon.
5 Comments
Reading the sheer number of these articles that keep coming through, I have to wonder about how long the web will remain useful beyond the most basic functions - and maybe not even then.
Maybe the good people at MIT are right: https://www.technologyreview.com/2023/04/04/1070938/we-are-hurtling-tow…
Makes me think of Facebook, that.
A capthca asking you to press the windows + R key and then ctrl v should be a huge red flag no?
(On a related note, has anyone else found capthcas harder and harder to get through? E.g. when it asks you to click on "traffic lights" does that include the "arm" the lights are held on? I often find that there are little bits of stairs or motorcyles on one square but am not sure whether it wants you to select those or not. I end up having to do 5 or 6 captchas. Maybe I'm just overthinking it?)
No, you're right, they are getting harder.
It makes me wonder if we're going to end up using physical (i.e. printed) one time pads for on line applications.
It flies in the face of futuristic digital security, but it is very hard to defeat and it feels like a retrograde step that's required to prevent malfeasance - much like having to return to hand-written examinations under invigilation to stop cheating.

We welcome your comments below. If you are not already registered, please register to comment
Remember we welcome robust, respectful and insightful debate. We don't welcome abusive or defamatory comments and will de-register those repeatedly making such comments. Our current comment policy is here.