
New Zealanders lost $6.8 million to cybercrime in the final quarter of 2024, marking a 24 per cent increase from the previous quarter, the National Cyber Security Centre's latest Cyber Security Insights report says. This despite the overall number of incidents in the quarter dropping sharply compared to the previous one.
The report, covers October to December 2024, and lists a record 17 incidents with losses exceeding $100,000, accounting for $4.7 million of the total financial damage.
"This is the largest number of high-loss incidents we have seen in a quarter," Tom Roberts, NCSC threat and incident response team lead, said on the release of the report.
"These incidents are also quite varied — ranging from cyber attacks on computers and accounts, to cyber-enabled scams," he added.
Many of these significant breaches began with phone calls from individuals impersonating legitimate organisations, Roberts noted.
Despite the financial toll rising, the overall number of reported incidents dropped by 34 per cent compared to the previous quarter. Phishing and credential harvesting reports saw the most dramatic decline, falling 54 per cent.
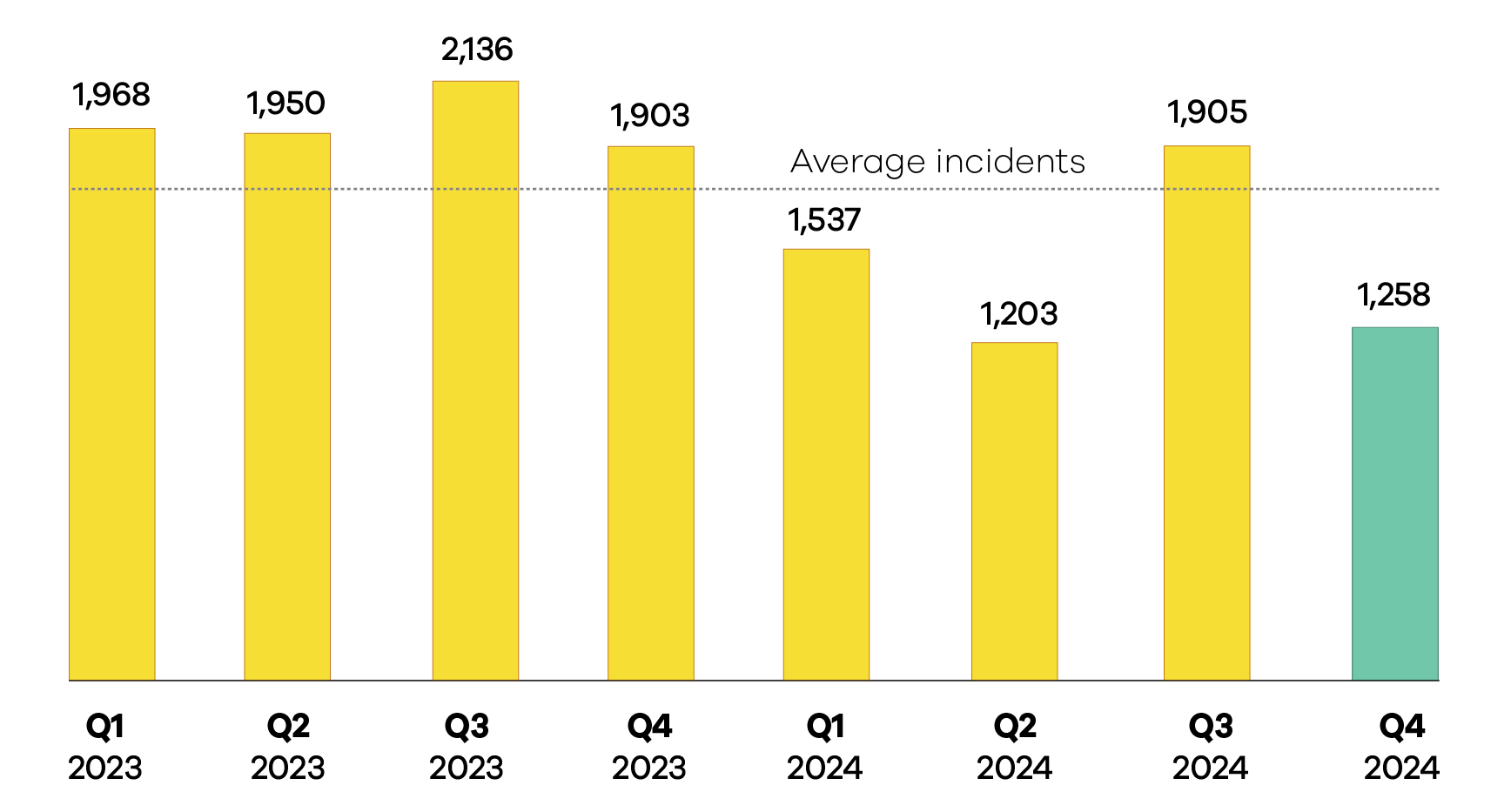
"A decrease in numbers doesn't mean there's less cybercrime," Roberts, NCSC threat and incident response team lead, said.
"We know cybercrime is underreported and we need your reports to better understand and respond to the threats New Zealand faces."
The $6.8 million in direct financial losses represents a 91 per cent increase compared to the same period in 2023. Overall, the recorded average losses for 2024 were higher than for 2023.
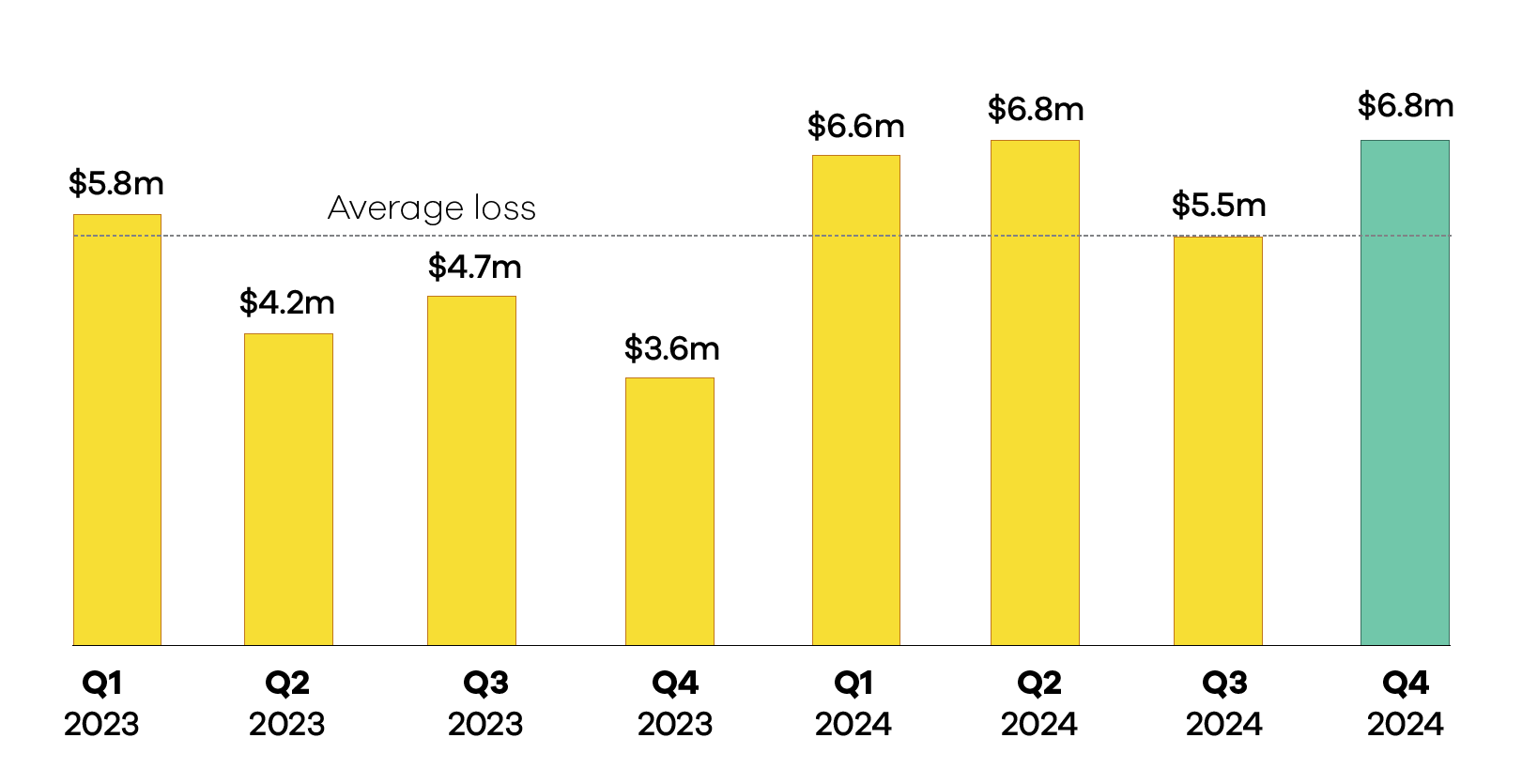
Scams and fraud overtook phishing as the most commonly reported category, despite a 15 per cent decrease in such incidents from the previous quarter.
Fewer nation-state attacks in the quarter
The NCSC recorded 1358 incident reports during the quarter. Of these, 100 required specialist technical support due to their potential national significance, slightly up from 98 in the previous quarter.
Of the 100 incidents of national significance, four were classified as C3 which is "significant". While no detailed breakdown was provided of the C3 incidents, NCSC/CERT NZ said they included unusual distributed denial-of-service (DDoS) against organisations in the financial sector, and a ransomware incident that impacted the customer services of an organisation in the information media and telecommunications sector.
Attributing incidents to particular threat actors is notoriously difficult even for cyber security experts, but NCSC/CERT NZ said that 21 of the 100 incidents above were linked to state-sponsored hackers. Cyber criminals were likely behind 36 of the attacks, with NCSC/CERT NZ not finding sufficient evidence in 43 cases to link the activity to a known threat.
The figures of probable state-sponsored attacks are 30 per cent compared to a typical quarter
No C1 or C2 incidents were recored in the quarter.
The NCSC encourages all New Zealanders to report cyber incidents to help protect others from similar attacks. Phishing emails can be forwarded to phishpond@ops.cert.govt.nz for analysis by NCSC.

We welcome your comments below. If you are not already registered, please register to comment
Remember we welcome robust, respectful and insightful debate. We don't welcome abusive or defamatory comments and will de-register those repeatedly making such comments. Our current comment policy is here.