
Over on Facebook, people are worried about a new menace that hasn't yet arrived in New Zealand: receiving unexpected packages that contain gifts and a QR code to scan to see who sent it. Beware of geeks bearing gifts! Well, scammers sending them at least.
New Zealand Police are warning people about the scam, which they expect to arrive in the country, which is highly likely to happen.
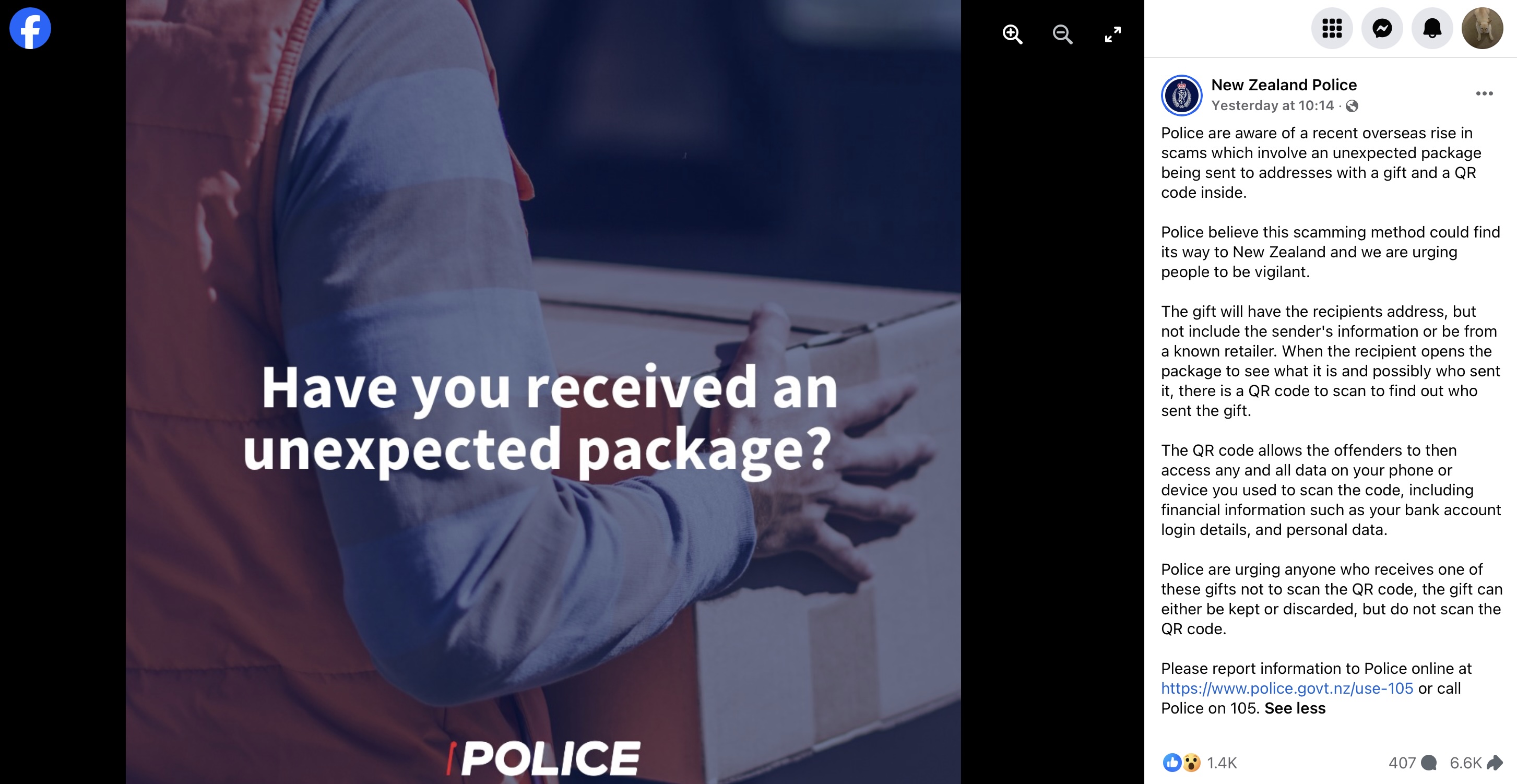
Unfortunately, the warning has people overly concerned, as it appears to be missing a step in the exploitation process. NZ Police said; "the QR code allows the offenders to then access any and all data on your phone or device you used to scan, including financial details such as your bank account login details, and personal data."
That was news. While Quick Response codes store data in a clever way, being able to weaponise them as per above would make them very dangerous indeed, to the point that eg. phone makers would be well advised to remove support for them. Now that would be something very big indeed.
What's going on then? Checking in with the Police for a more detailed explanation produced a response referring to a recent United States Federal Bureau of Investigation (FBI) Internet Crime Centre (IC3) advisory.
Here's the crucial part of what could happen if you scan a malicious QR code:
"In reality, the QR code may take you to a malicious website."
The Police and overseas law enforcement are right to warn users about malicious QR codes of course. QR codes are everywhere, and we've been conditioned to trust and scan them, just like opening email attachments makes them such an effective attack vector.
However, QR codes are not inherently harmful, in the same manner that links to websites are not. It all depends on the target destination, and if your device is set to act on the information stored in the QR code by, for example, launching apps.
For a demonstration of how it works, scan the QR code accompanying this story. Many web browsers will automatically recognise QR codes as well, but humans can't see the data they contain with the naked eye. Because of that, and the ease at which they can be generated, some attackers have taken to creating malicious QR codes on stickers that they paste over legit ones - like the ones used to pay for parking.

Processing data from untrusted sources carries a risk. As an example, security vendor ESET analysed a threat used to target Telegram users with Google Android phones recently, with malicious files masquerading as videos. QR codes can hold around 3 kilobytes of data which isn't a huge amount, but a creative attacker could make good use of it.
This type of attack has of course a catchy name, Quishing. There is a related scam called Brushing, which the United States Postal Inspection Service (USPIS) describes as this:
"A person receives packages or parcels containing various sorts of items which were not ordered or requested by the recipient. While the package may be addressed to the recipient, there is not a return address, or the return address could be that of a retailer. The sender of the item(s) is usually an international, third-party seller who has found the recipient’s address online.
The intention is to give the impression that the recipient is a verified buyer who has written positive online reviews of the merchandise, meaning: they write a fake review in your name. These fake reviews help to fraudulently boost or inflate the products’ ratings and sales numbers, which they hope results in an increase of actual sales in the long-run. Since the merchandise is usually cheap and low-cost to ship, the scammers perceive this as a profitable pay-off."
Either way, the Internet is a very hostile environment these days so be careful what sites you visit. Scammers have for years now exploited the very simple technique of creating trustworthy-looking destinations and asking people to log in to them with their credentials, which are then captured. Should that happen, it's game over, bad times ahead so be very suspicious if you encounter that.
What's not covered in the law enforcement advisories is the economics of the scams. Surely it must cost a pretty penny to source gifts, get them packed up and send them to a goodly amount of victims? Physical couriering like that ought to be traceable as well.
5 Comments
The comments section of interest.co.nz real estate articles can be very hostile.
Raw - surfer beware…….
For a long time we trained people not to click dodgy links. Then somehow we did a 180 and we trained people to start clicking dodgy links (disguised as QR codes). The covid experience introduced a lot of older people (especially) to QR codes, and has a lot to answer for in this regard.
No, that's disinformation and off topic. QR codes were used because they were already very popular and almost everyone knew how to use them. Otherwise the whole tracing system wouldn't have worked.
QR codes are a useful way to bridge the analogue - digital divide, and this parasitization by malign actors is disheartening news.
It really does look like the web, beyond a few basic functions, is going to eat itself.

We welcome your comments below. If you are not already registered, please register to comment
Remember we welcome robust, respectful and insightful debate. We don't welcome abusive or defamatory comments and will de-register those repeatedly making such comments. Our current comment policy is here.