
Letting old technology connect to unknown networks is never a good idea and here's a great example of that, courtesy of Google's Android security and privacy team, involving reaching too far back in time than what is safe.
Even newer 5G smartphones are able to drop down to the now ancient 2G standard, which was first implemented in Finland 33 years ago. That's called "backwards compatibility" in tech jargon, and on the face of it, a useful feature providing connectivity in case the newer mobile radio signalling protocols are not available.
However, using 2G also means you open up a can of vulnerabilities.
Enter the SMS Blasters! As the name implies, these devices are as Google says readily available on the Internet and are easy for attackers to use, to fire off Short Messaging Service (SMS) text message spam campaigns.
Said SMS Blasters are basically miniature cellular phone sites, often called Stingrays, Dirtboxes, IMSI (International Mobile Subscriber Identity, a code that IDs every phone user on a network) catchers, and rogue or false base stations (RFBs and FBSs).
They're small enough to fit into backpacks, and perfect to carry around in public spaces. SMS Blaster attacks also give a new meaning to "war driving" a term which the older geeks in the audience will recognise (I hope).
An SMS Blaster activates a bogus 4G or 5G network, that does one thing only: it tells a victim's phone to downgrade to 2G, and offers up a network running that old mobile signalling standard to connect to.
The attack drops newer security features in newer protocols such as mutual authentication, Google says, and forces connections to be unencrypted.
This enables Person-in-the-Middle (PitM) attacks to inject SMS payloads. Massive malicious campaigns are possible easily and cheaply, with hundreds of thousands of messages being sent.
Phishing, public safety alerts, you name it.
Attackers can do pretty much anything possible with SMS attacks, as they're bypassing the telco networks and able to send fully fake messages pretending to be legit senders, as they're not filtered at all.
As you can imagine, this type of attack is liable to become popular, and Google said they're taking place in lots of countries, such as France, Norway, Thailand and Vietnam.
Google is now relaying the mobile phone industry organisation GSMA's fraud and security group's warning about SMS Blasters targeting Android phones, but the vulnerability is there in any phone that supports 2G.
The 2G vulnerability has been known for some years now, exacerbated by lack of awareness and more importantly, users not being able to turn off support for the older protocol.
There will no doubt be defensive messaging from telco industry organisations on this soon, explaining how they take subscriber security seriously and why they haven't, as it appears, been slack and slow to respond effectively to a really bad vulnerability that affects millions of users around the world.
Google said that from Android version 12 running on devices that follow the Radio HAL (hardware abstraction layer) 1.6+ specification, users can turn off 2G support; Android 14 on devices with Radio HAL 2.0 and higher can also switch off the null cipher feature that enables 2G SMS Blasters to transmit payloads to smartphones.
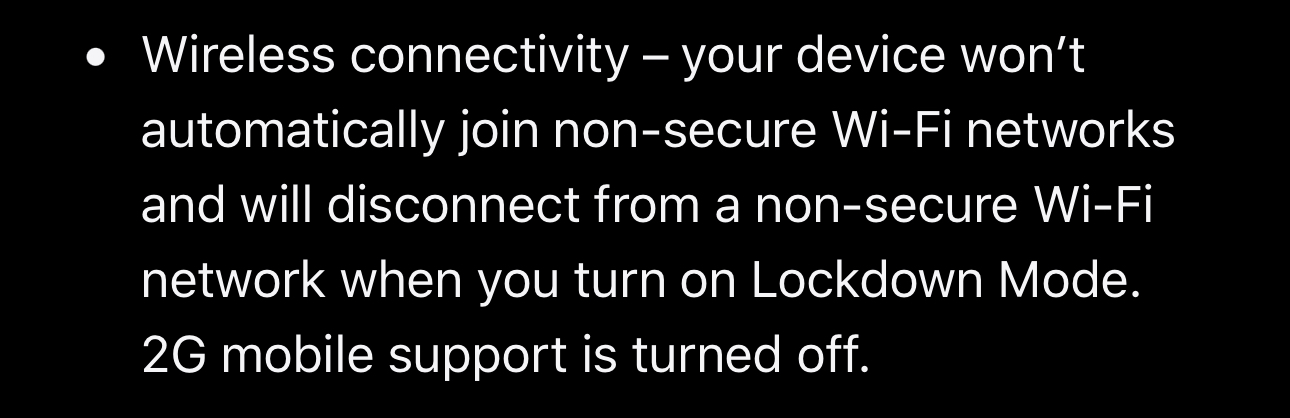
Apple doesn't provide the same level of control, but enabling Lockdown Mode disables 2G at the cost of functionality loss.
Long story short, if you were looking for a reason to upgrade your phone, being able to do away with 2G support seems quite high on the list. Not that upgrading will work in every case. Last year, the Electronic Frontier Foundation looked into the issue, and weren't impressed with Samsung not implementing the Android security measures of being able to turn off 2G and/or disabling null ciphers (which switch off encryption).
19 Comments
Anyone know how to do this on Samsung? I can't find the setting
It should be a matter of Android, not Samsung. Something like Settings > Connections > Mobile Networks > Network Mode.
However I'm only given the choice of 4G/3G/2G, 3G/2G, 3G Only, and 2G Only. I'mr running a pretty basic phone though, I don't really like participating in a high tech world...
Same as my Samsung, there is no option to turn off the 2G. My phone is still getting updates so not really worried about it as Samsung seems a whole lot less vulnerable that an iPhone. Running Android 13. Even 3G is being turned off in 2025.
Seems samsungs phone don't have the option in most markets (incl NZ). Which would be a useful bit of information in the article, really.
Did you read the last paragraph?
Yeah those are the same options I see. No option to turn off 2G unless choosing 3G only
Same here on the old S22 flagship, andriod 14.
On Google Pixel phones the turn off 2G setting is associated with the sim card setting, not the global use 5 4 3G network settings. It's been like that since Android 13 beta and is off by default in my current Android 15.
I would have thought Samsung would do it in the same way , although they do tend to be very slow with implementing android updates
Based on the article, Samsung may have chosen not to implement that feature
Last year, the Electronic Frontier Foundation looked into the issue, and weren't impressed with Samsung not implementing the Android security measures of being able to turn off 2G and/or disabling null ciphers (which switch off encryption).
"@Daniel00011 is correct, 2G is used for Voice and text, turning it off may result in you not getting calls and text" except via wifi?
Is this correct in NZ ??
Samsung don't let you turn it off anyway
No, it's not.
The days of falling back to 2g for calls are long gone. I think there's only telecom that still actually has 2g turned on, and they are turning it off soon. The vector subcontractors were around recently to replace the 2g modem in our power meter.
I think the point of the article is that the network you're connected to is irrelevant. What can happen is that a device when in range can be used to trick your phone to drop down to 2G, which has vulnerabilities that can be exploited. And as some of us are finding out here, Samsung (I'm on android 14, A52s) will only allow you to specify 3G only as an option to lock off 2G capability. If you want 5G or 4G hook up to the mobile network, then you are forced to also allow 2G and 3G.
Agreed, my point was in relation to the OP claims that 2g is still needed for voice and text.
Google Pixel phones Android 14 and 15 have had the use 2G service off by default since 14 beta. Samsung are very slow to implement these basic changes unfortunately.
It's One NZ that still has 2g based on their coverage map, Spark's doesn't have a 2g option, and I don't think 2degrees ever had 2g, though may have let you use one of the other carrier's 2g networks as a fallback in the early days.
So if you're on One NZ or a MVNO that uses One NZ such as Kogan it may limit where you have signal
2degrees had 2g, but as they are short on frequencies they were the first to turn it off
"war driving" - LOL. Yip. Remember that. Back in the day when internet was hugely expensive.
On Google Pixel phones 2G support is off by default. I guess it depends on how Samsung implement Android as to what they do.
The google version of Android has had the 2G warning on the settings menu for some time. I'm not sure why anyone would even have 2G turned on anyway.

We welcome your comments below. If you are not already registered, please register to comment
Remember we welcome robust, respectful and insightful debate. We don't welcome abusive or defamatory comments and will de-register those repeatedly making such comments. Our current comment policy is here.