
Recently, there was a discussion thread on LinkedIn suggesting you can't use a password manager for internet banking. Why exactly wasn't quite clear, but it seemed to be an interpretation of "memorising" the passphrase versus writing it down.
This seemed odd, as password managers are everywhere, from web browsers to standalone apps, and built into operating systems. Security researchers recommend using password managers, and to be honest, with the ever-growing number of logins for services and apps, how could anyone survive without one?
Furthermore, how would a bank know that you're using a password manager?
It is an important point to clarify though, so I asked ASB. A spokesperson for the bank sent this response:
Under ASB’s Terms and Conditions, our customers must take responsibility for and protect their personal information and Security Credentials, such as PINs, log-in and password details.
Security Credentials should remain confidential to each customer and should be memorised, must not be written down or disclosed to anyone else. If a customer suspects their Security Credentials have been disclosed to another person, this must be reported as soon as the customer is aware or suspects the information has been compromised.
CERT NZ recommends using a password manager to keep data safe and protect passwords. We are supportive of using reputable password managers that encrypt data, alongside the other safety measures outlined by CERT NZ.
That's commonsense from both ASB and the government Computer Emergency Response Team (CERT).
If your bank grinds its gears over password manager use, it's a sign they haven't kept up with the times and should rethink their opposition to a tool that can enhance customer security.
How do password managers enhance security then? Any sensible service provider will set a password policy for access that requires a reasonably complex "Open Sesame" phrase that's difficult to guess, or crack as information security pros call it. If they don't, go somewhere else.
Now, if you want to make it harder for miscreants to guess your password, take a look at the below table:
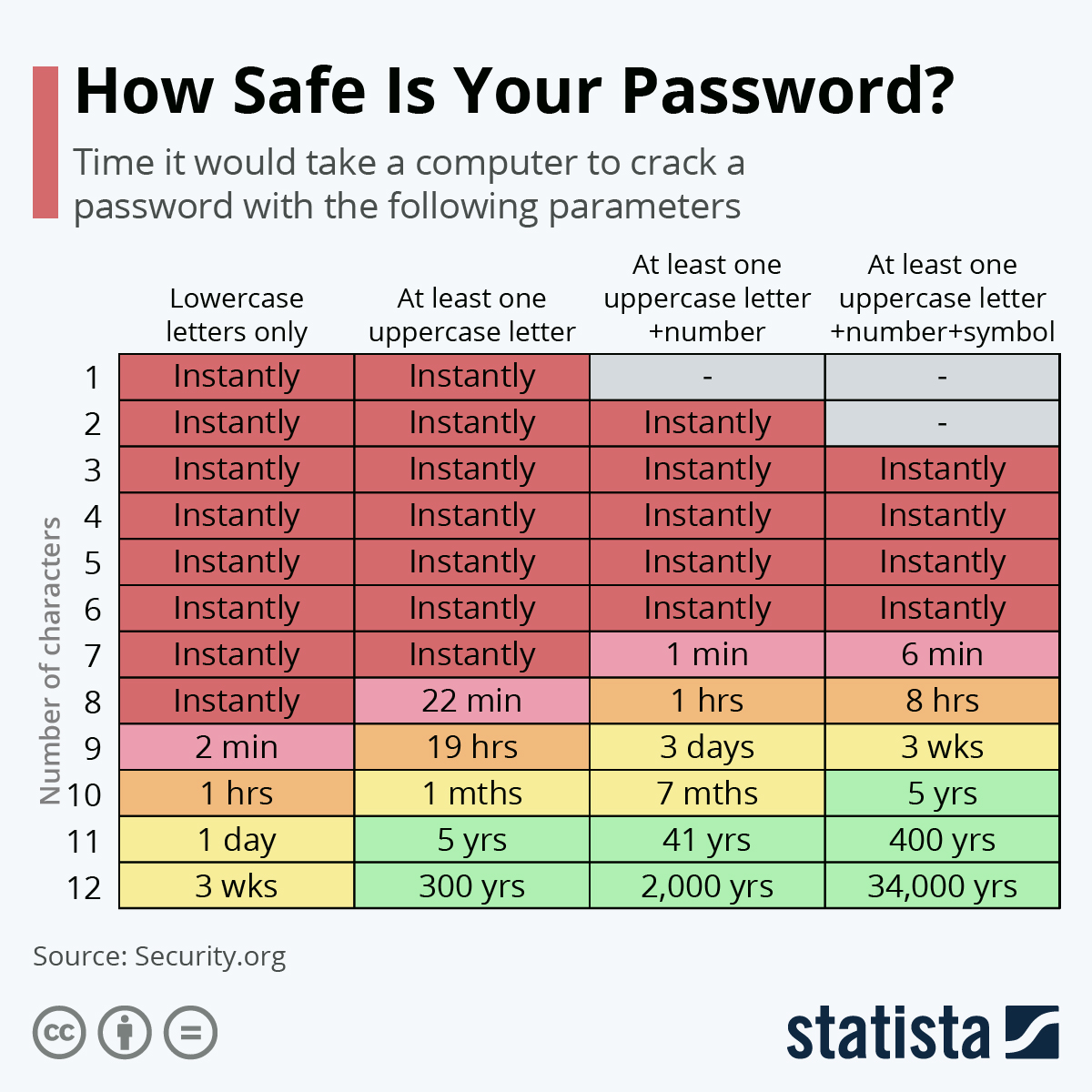
As a related aside, a properly configured access system will slam the brakes on repeated passphrase guesses and when too many have been entered, lock the login and force an account reset.
Back to longer and complex passwords: they are not only difficult to guess, but hard for users to remember as well. The temptation here is to use a simple one (if the site in question allows it) or to reuse a password that you can remember. Both are really bad ideas, for obvious reasons, but there's a persistent, false assumption that "it won't happen to me".
On Apple's macOS, the built-in password manager offers a range of features that makes life easier and more secure. The tool creates complex, hard-to-guess passwords (natch) that are unique to each site, to avoid re-use of credentials. By tapping the Touch ID biometric fingerprint sensor on my MacBook, logins are painless and quick with the credentials being filled in for you.
Better yet, the macOS password manager audits existing passwords, and warns if they've been reused or found in data breaches.
You'll find similar features in other password managers but absolutely follow CERT NZ and ASB's recommendation to use a reputable one that encrypts stored credentials. As you can imagine, password managers are attacker targets and if they are breached, things can get scary.
It follows from there that having multiple safeguards to protect our digital lives should things go wrong is not a bad idea at all. Think of it like washing skyscraper windows, and being secured with more than one rope for when that inevitable miss-step happens.
Have a read of our piece on multi-factor authentication (MFA) with some thoughts on how to up your security game.
40 Comments
You broke Betteridges Law, I came in here expecting to find out why I shouldn't be using a password manager.
I'm really liking that most password managers now seem to produce phrases rather than random character strings, you end up with a password with heaps of entropy and super easy to memorise.
You hope they would, forcing less complex passwords for cracking but difficult for humans to remember often leads to less secure ones from the outset as humans tend to simplicity. This disconnect has led to an explosion in third party password storage which is also even less secure on many different levels. Whereas passwords with more difficulty to crack & easier to remember passwords are far more ideal from a corporate security perspective.
However 2+ factor should be default instead of implementing password restrictions to force users to passwords that are easier to crack. That being the case though it needs to be said biometrics & face ID are not as useful as people hope as they can be cracked by family easily without effort (those most likely to abuse & even kill you), and if a person has cheap super glue then prints are not an issue either. Anything offering a pin entry should be shamed.
Also the banks have a massive security hole already in Paywave. Arguing about passwords when a wave of the hand can steal money freely without impediment for a large number of iterations is kind of trying to bolt the barn door after the horse has bolted with all the money in your cash account.
Another reason why I left Avast.
But let's face it, we should all be able to create our own relatively unbreakable passwords for the password managers to save. Ones with proper nouns that require a capital.
Not my banking password, but should have been a contender :
"Ooh $10. Aw I wanted a peanut."
30 characters including specials, upper and lowercase and spaces. Unforgettable.
We could but can everyone? The issue of the human drive for simplicity is that it is a hard bias to beat. Hence why so many resort to us vs them, black vs white thought patterns instead of recognizing the shades of grey or complexities. It is really hard for most humans to accommodate more complexity. Many cannot even grasp multiple sides in simple arguments or a third viewpoint (or any other then their own). Adding punctuation in, sentence structure can be harder then say remembering the line to a favourite show without. e.g. "what is your mothers maiden name what is her first name I just knew her as ma" (appropriate reference)
We have to consider most people in the design for security measures. Most people are sadly far more often going to want more simple passwords to remember and simple is far less then what you and I expect. Nowadays many want even no password entry, hold up a photo and you are in type entry, or even mobile always logged in entry they can carry and lose at any time, like a paywave card. Designing for that is always going to mean we need more then a first level of defense (a password or biometrics) and to have backup security options or policies because any account is susceptible to attack, none are truly fully secure; we need the next steps planned out after an account has been breached.
Consider this scenario ...
1. You open your laptop ...
2. You enter your PIN of 4 characters - or 6 or 8 or 10 or whatever
3. Someone is surreptitiously filming your hand movements with a mobile device
4. You're called away to a meeting so you lock your laptop but leave it on your desk.
5. The person filming has watched the video and knows your PIN
6. They logon to the lap top and all your passwords are available thanks to the password manager
This was a real life scenario that resulted in theft. I had to prove that this actually occurred.
The laptop user could have used biometrics (the finger print scanner, retina recognition, facial recognition, etc.) to achieve two factor authentication- but didn't because it was unreliable. They also could have set up multiple password managers to handle sensitive and non-sensitive passwords.
Call me old fashioned - but I memorize passwords to sensitive sites. But for everything non-sensitive a password manager is pretty good (but only if you properly log off a site and/or the site does this rigorously for you).
As an aside - some years ago we used to use high end video cards to do brute force hacks on passwords stored anywhere on disk in the known locations. Does anyone still do this?
Always expect a man in the middle somewhere, getting the master password is simply 1 more easy step after access to the device is given (the master password is still typed or entered via biometrics etc). Sadly though no one expects the Spanish inquisition.
Ideally you want the bank to require more factors of authentication for transactions then read data requests. Also adding custom-to-the-user random problems solved when a user has already provided password access is good for account entry checks. In the case where multiple devices are stolen e.g. your luggage, wallet and mobile in a low effort mugging that threatens fingers for the initial login you probably want a bank to be prepared to help retrieve your own access and re-secure your accounts again afterwards.
Er yeah not surprising. Much like how a computer solely designed for games should be good for gaming. Or a computer solely designed for pressure and depth readings would be better for diving then a mobile phone even though the latter has more computing power.
It is kind of a tautology. It should be better, only with murphy's law or severe financial restrictions could it be worse.
If the mining rig did not perform as well as a good graphics card in mining that is just shamefully poor engineering design or very cheap tech.
Physical access is a "game over" scenario in most cases, but for example the macOS password manager isn't open by default even if you're logged in. You have to authenticate again, with biometrics or the system password at least. Yes, video cards are great for not just AI and games, but also for brute-force password cracking. I know of people who build rigs with eight or more cards in them. They have a reason to do that.
"Physical access is a "game over" scenario in most cases... "
Oh how I wish that were so. I really do. But as soon as the device is connected to a network, "physical access" becomes a whole different ballgame.
But yes. Protecting one's device, and who can "access it" is what it all about.
Fun fact Apple only recently fixed the bug in macOS High Sierra that if you entered no password for a root account and pressed enter a few times it automatically logged you in with administrator access. It was still out and about and in the wild for many Apple Macs for years after the release. https://arstechnica.com/information-technology/2017/11/macos-bug-lets-y… It also in computers with remote options turned on, (e.g. use remote access apps) allowed attackers to remotely access the machine with no password required
I tested this on a few Mac machines after the patch was released (and these computers in different offices were supposedly updated) and yeah it was not great I could login just by spamming an empty password a few times. It was like I was asking the device to sudo let me in and make me a sandwich.
Here's hoping this was a lesson learned for Apple's security team that all access pass with a few clicks of the mouse is not a good idea in the later OS releases.
Oh boy, can this article please be removed? This is bad advice.
If the bank says do not use a password manager, then people should be aware of the risks involved before even considering using one.
Late 2022, early 2023, a major password manager was hacked, their "vault" was compromised and although the bank may have security measures to flag brute force attempts, the vault, once in the hands of hackers, does not. They are then able to brute force the vault using users master passwords and access all of the profiles contained passwords directly. Meaning, if your account becomes compromised in this situation, they could simply access and enter the correct username and password a single time to access your banking accounts rendering all of the banks security measures useless - other than IP based restrictions (VPN anyone?) and MFA.
There are password managers who offer better security than others, but at the end of the day memorising your bank password is the single best security measure as you are not storing the password anywhere which can be potentially accessed, such as a password manager, as has happened, and will happen again.
Actually is that corrrect? I surely would not be disclosing my bank password to the password manager - isn't the password manager generating a password for me? If so then how does that match with what the bank expects? Back to being confused !!. Can someone clarify how these things work.
The password manager is your agent. I.e. you empowered the agent, thus your problem.
You'd need to prove your password manager ceased to become your agent before anyone would listen. I.e. your password manager had been hacked. And then the counter claim would be that you installed it - and trusted it - so still your problem.
Here are two links you may find useful:
If your bank focuses on passwords instead of implementing proper 2 or 3 factor logins and security checks for key monetary movements then you know you are with a bad bank. Even a 15+ password of multiple character types is only limited security and can easily be taken.
The reason I wouldn't use a password manager for my bank is simple especially if its across multiple devices.
You are storing you password in a decryptable format on the internet, while the password will most likely be much more complex than one that you can remember, that password management service is a massive target for hackers. If you even trust the company that provides that password manager, have you investigated them? Have you any idea how they keep your data safe. Having worked and written software for banks I would not consider and other companies that keep data secure I would not say they do a very good job.
While the the statistics for cracking a password are probably accurate this requires the attacker to have already broken into your bank and stolen the password file. Any good system will lock out a user after a few attempts tying the incorrect password. If you believe your bank can be hacked, why don't you believe the company that manages your password manger can't be? Passwords in a bank SHOULD be one way hashed, passwords in a password manger have to be decryptable since they need to send that information to the server to log in.
I have to trust the creator of my operating system, browser, and my bank because I have no choice but the fewer people I trust with my bank password the better.
Frankly passwords are a dumb idea, for high security applications like banking, also bio-metrics are too (the problem there is once they are compromised you cannot change them)
Frankly challenge response mechanism with a non programmable device where not even the bank knows the private key is the best alternative, sure you can add a password or some bio-metrics so you stop some random person picking the device up and using it.
Once you put your 2 factor authentication, or you password on a programmable internet connected device like a phone you are opening up a the attack surface by a lot.

We welcome your comments below. If you are not already registered, please register to comment.
Remember we welcome robust, respectful and insightful debate. We don't welcome abusive or defamatory comments and will de-register those repeatedly making such comments. Our current comment policy is here.